
Dr. Madan Mohan
A large number of modern organizations are becoming "leaner" and increasingly dependent on their supply chain; the external services, processes, or components that aid your company's production. The supply chain is critical to the achievement of your organization's objectives, and unfortunately, the preferred attack centers for attackers. A dependence on external factors for supply chain management causes your organization to be vulnerable to a wide range of cyber-threats that may harm your organization and its activity.
A research in Gartner says “Third parties have greater access to organizational data assets and are working with an increasing number of third parties”. In 2019, 71% of organizations report their third-party network contains more third parties than it did three years ago, and the same percentage reports their third-party network will grow even larger in the next three years. In fact, their research shows that 60% of organizations are now working with more than 1,000 third parties.
The early identification of the threats that may arise from one supply chain or another, assessing the concrete risks of the organization in working with suppliers, assessing the existing controls for these risks and managing them become a necessary condition for achieving the organization's goals and resistance to cyber events.
In order to ensure you can achieve your organization's goals and be resilient in the case of a cyber-attack, your organization needs to identify the threats that may arise from your supply chain, assess the concrete risks to your organization through working with each supplier, and assess the existing controls for these risks as well as create a plan to manage them.
BDO has developed an innovative and unique service for handling supply chain risks of various types in every field. The service provides a complete solution for your organization; our cyber experts evaluate your supply chain and solve for all of your vulnerabilities, dealing with regulatory issues and internal organizational issues for you.
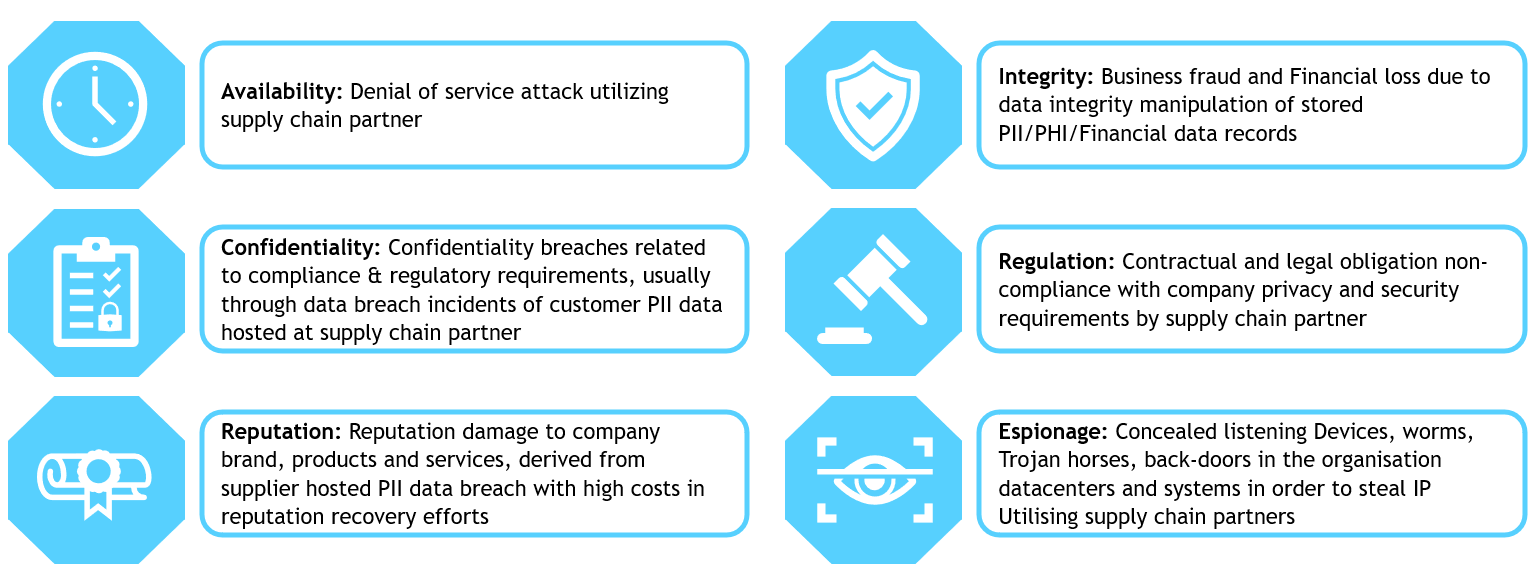
Following are the risk faced by the organisations in managing third-parties:
Our VCRM service includes: