
Dr. Madan Mohan
As a business grows, information sharing grows along with it – with vendors, contractors, partners, and customers. Every one of these digital relationships presents a new set of cyber risks. The need for security and the way in which it is implemented must be balanced in line with the needs of an organisation to operate effectively and to pursue its future goals actively. While it is impossible to eliminate all risks of cyber-attacks, a well-designed program will minimise the negative impact on both short and long-term business goals.
BDO has a team of information and cybersecurity experts which, along with our investment in tools and methods, can help bring the latest insights to your business. BDO’s cybersecurity services offer a number of different solutions, from high-level assessments to more in-depth intrusive assessment of the security configurations. Our team is comprised of seasoned professionals from a diverse range of backgrounds, including experienced IT, operations and data privacy consultants, as well as forensic technology professionals. We are built to provide comprehensive, customised services for each client, focusing on your specific operating model, technical demands, regulatory environment, and industry dynamics. Whether it’s financial services, telecoms, oil & gas, government entity, insurance, healthcare, retail, hospitality, or any other industry – we understand your needs.
We will conduct the vulnerability assessment and penetration testing in three ways:
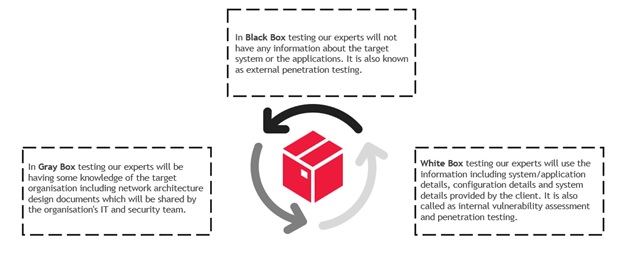
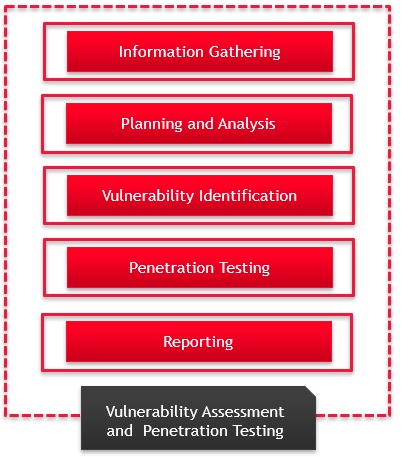
Our approach for vulnerability assessment and penetration testing (VAPT)
.jpg.aspx?width=300&height=328)
BDO provides the following range of cybersecurity services: