
Dr. Madan Mohan
Red teaming is the act of thoroughly testing and challenging the organisation’s cybersecurity strategy, plans, policies and systems from the perspective of an adversary. Red teaming simulates real world attacks and tests organisation’s ability to identify the current security weaknesses and how well the organisation is prepared to handle and mitigate the cyber threats in any form.
Red teaming is a robust means to provide the management with factual assessment of an organization’s information security environment. A highly trained and experienced specialists along with white hat hackers come together to establish this special team who consider all aspects of people, process and technology areas. This exercise is essential for Chief information security officer (CISO)/Management to clearly understand the effectiveness of security budget and its utilization in securing organization’s critical assets. It also highlights the areas which requires attention to further strengthen the cyber-defense of the organization.
While performing these exercises, we will mimic the threat actor’s activities to uncover the cyber risks (including data theft, data breach, unavailability of systems, etc.) and it’s impact on the organisation’s information security ecosystem. We ensure that the red teaming activities are performed in a controlled manner without affecting the organisation’s information assets. Our approach to conduct red teaming exercises is described below:
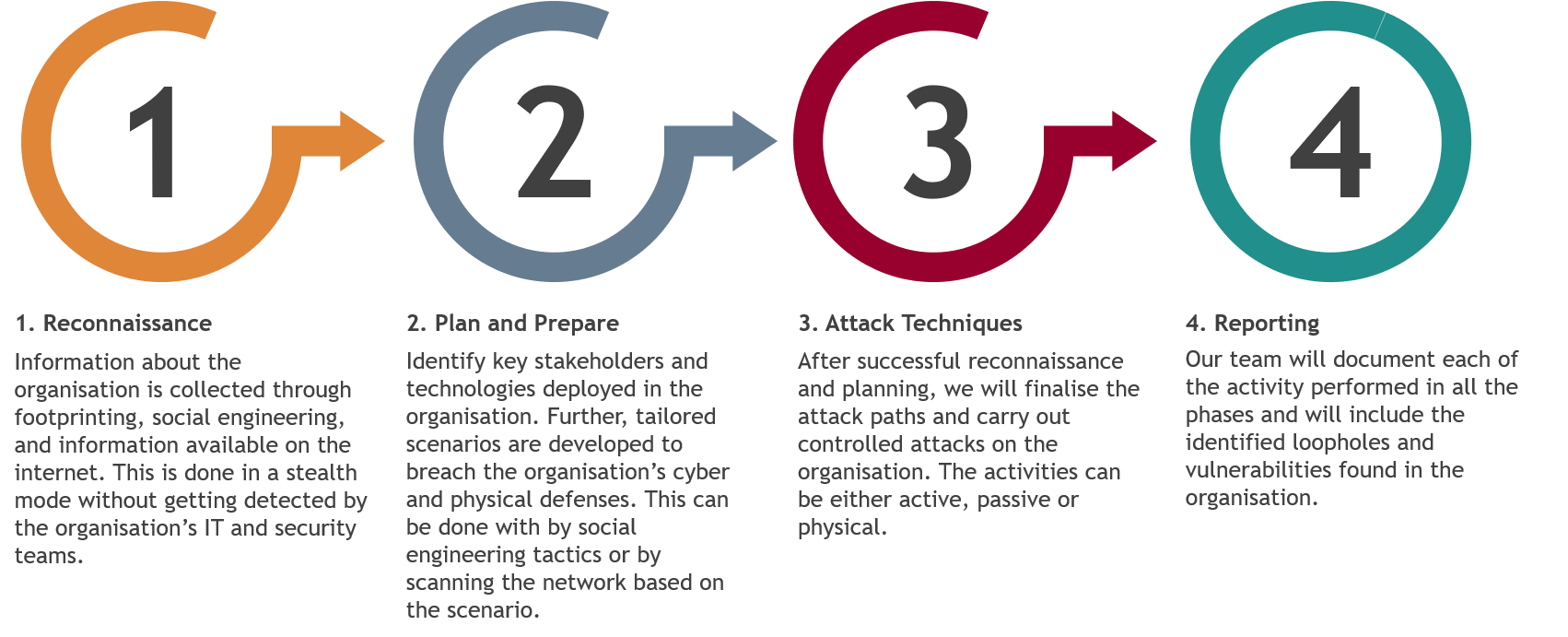
Attack techniques are described below:
Our deliverables will include reporting of each activities along with short term tactical fixes for immediate remediation and long-term strategic measures to holistically develop/strengthen organisation’s cyber defenses.